Mastering ConfigMaps and Secrets in Kubernetes🔒🔑🛡️
Day 35 of 90daysofdevops
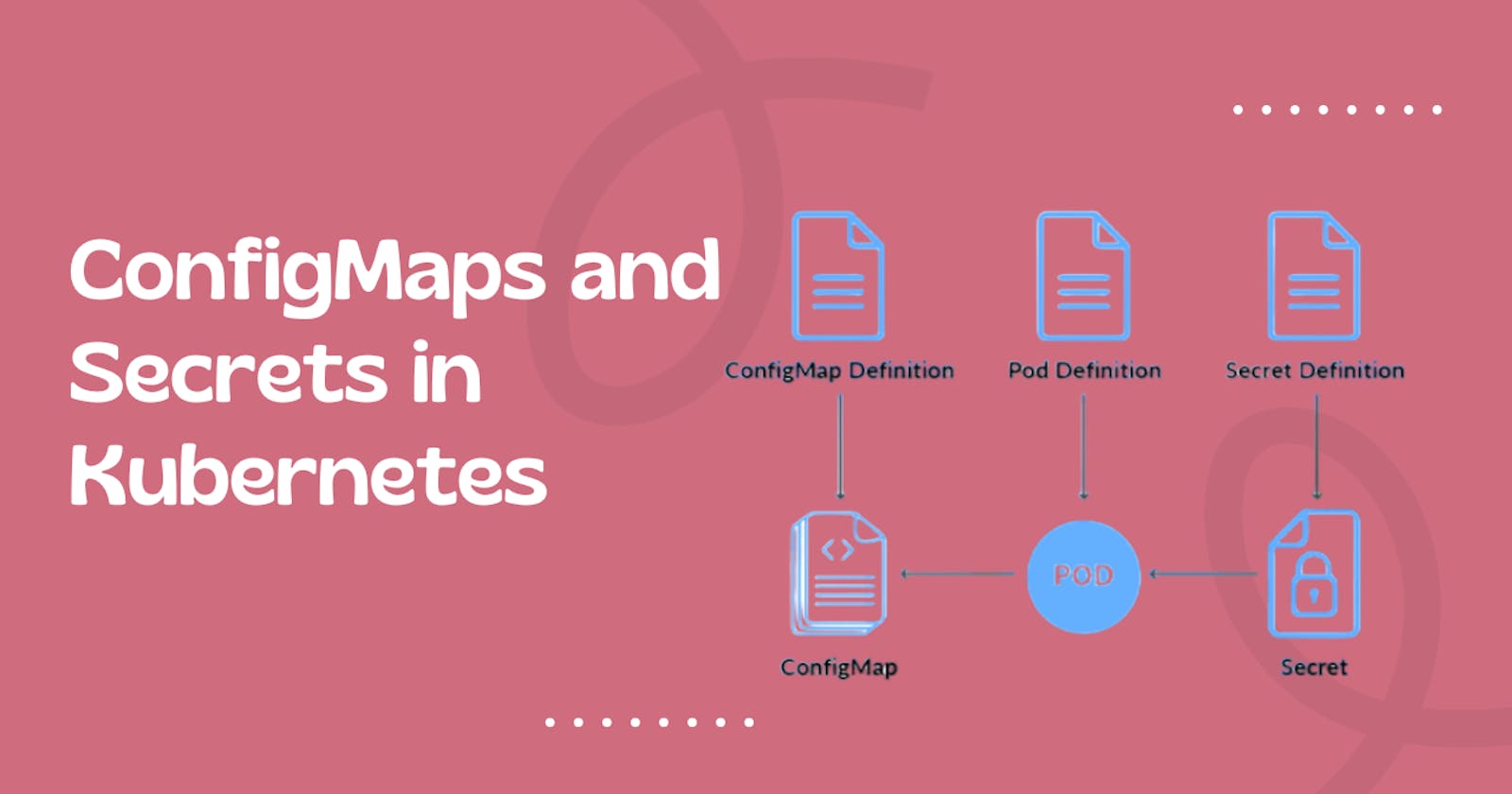
Define ConfigMaps
ConfigMaps in Kubernetes is a way to store configuration data as key-value pairs or plain text files, separate from the application code.
ConfigMaps can be used to store environment variables, configuration files, command-line arguments, or any other configuration data required by an application.
ConfigMaps can be created manually using the Kubernetes CLI or YAML files, or they can be generated automatically from configuration files or directories using the Kubernetes API.
When a ConfigMap is created, it can be mounted as a volume or used as environment variables in a Pod. The data in the ConfigMap can be updated independently of the application code, allowing for dynamic configuration changes without redeploying the application.
ConfigMaps are useful for managing the configuration of applications running in Kubernetes, particularly in microservices architectures where many small services may have their own unique configuration requirements.
By centralizing configuration data in ConfigMaps, it becomes easier to manage and update configurations across multiple services, without the need for complex scripting or manual intervention.
Define Secrets in K8s
Secrets in Kubernetes are similar to ConfigMaps, in that they are used to store and manage sensitive information, such as passwords, API keys, and certificates.
Secrets are designed specifically to keep this sensitive data secure, by encrypting it at rest and providing secure mechanisms for distributing and using the data.
When a Secret is created, the data is stored in an encrypted format and can be mounted as a volume or used as environment variables in a Pod. The data is encrypted using a key that is managed by Kubernetes and is only accessible to authorized users or processes.
Secrets are essential for managing sensitive information in Kubernetes, particularly in production environments where security is critical. By centralizing sensitive data in Secrets, it becomes easier to manage and update the data across multiple services, while ensuring that the data is kept secure at all times.
Set Up MySQL Client using ConfigMap & Secrets
Task 1:
Create a ConfigMap for your Deployment using a file or the command line.
vim configMap.yml
kind: ConfigMap apiVersion: v1 metadata: name: mysql-config labels: app: todo data: MYSQL_DB: "todo-db"
Now apply the configMap.
kubectl apply -f configMap.yml
Verify that the ConfigMap has been created by checking the status of the ConfigMaps in your Namespace.
The command shows the list of available configMap
kubectl get configmap
Task 2:
Create a Secret for your Deployment using a file or the command line
vim secrect.yml
apiVersion: v1 kind: Secret metadata: name: mysql-secret type: Opaque data: password: dHJhaW53aXRoc2h1YmhhbQ==
We can Encode & decode the Base64 key by ourselves.
# To Decode Base64 key echo "dHJhaW53aXRoc2h1YmhhbQ==" | base64 --decode # To Encode Base64 key echo "test@123" | base64
Now, apply the secret.
kubectl apply -f secret.yml
Verify that the Secret has been created by checking the status of the Secrets in your Namespace.
The command shows the list of available secrets
kubectl get secrets
Now update the deployment.yml file to include the configMap & Secret
apiVersion: apps/v1 kind: Deployment metadata: name: mysql labels: app: mysql spec: replicas: 1 selector: matchLabels: app: mysql template: metadata: labels: app: mysql spec: containers: - name: mysql image: mysql:8 ports: - containerPort: 3306 env: - name: MYSQL_ROOT_PASSWORD valueFrom: secretKeyRef: name: mysql-secret key: password - name: MYSQL_DATABASE valueFrom: configMapKeyRef: name: mysql-config key: MYSQL_DB
Apply the updated deployment using the command:
kubectl apply -f deployment.yml
To verify the MySQL pods are running, we can get the MySQL pod by running the following command.
kubectl get pods
To expose the MySQL use the K8s service, Create a service.yml file and make the configuration by headless service.
apiVersion: v1 kind: Service metadata: name: mysql-service spec: ports: - name: mysql port: 3306 clusterIP: None selector: app: mysql
Now apply for the service, so that the pod is exposed.
kubectl apply -f service.yml
Now on the Worker Node install the MySQL client on it.
sudo apt install mysql-client-core-8.0
Now connect the MySQL to the Master node using the below command
# Get inside of the mysql pod kubectl exec -it mysql-b7f864b95-nt24h /bin/sh # Now connect the mysql using username root and password from Secret mysql -u root -p${MYSQL_ROOT_PASSWORD}
Now we are finally in MySQL console, so we can do CRUD operation in it.
And use the todo-db that we had created before and that is listed in the databases.
Thank You,
I want to express my deepest gratitude to each and every one of you who has taken the time to read, engage, and support my journey.
Feel free to reach out to me if any corrections or add-ons are required on blogs. Your feedback is always welcome & appreciated.
~ Abhisek Moharana 😊